Azure MFA hard token and multi-device support
Towards the end of 2018 Microsoft announced that Azure MFA (the cloud offering) would support both hard tokens and up to 5 devices per user. Some enterprises still like hard tokens, these can be especially useful to support break-glass account types, were you can store the token in a secure physical location. Supporting multiple tokens can help ensure the account doesn’t get locked if the token gets damaged, though it does put an emphasis on keeping the tokens secure. So consider any additional audit requirements you might face with multiple tokens in multiple locations.
Previously to use a hard token you’d have to deploy an instance of Azure MFA Server which isn’t ideal as you need to pay for and manage infrastructure to support your MFA solution. In the world of cloud computing do you really want to have to do that? NO!!
I was curious to understand how to go about setting up hard tokens and multiple devices so I went ahead and bought some hard tokens to play with. Azure MFA supports OATH tokens that use time based one time passwords (TOTP) and there are a variety of manufacturers out there. I went for Token 2 (www.token2.com) as they offered tokens at a reasonable price and they stated they were Azure MFA compatible.
To use the Azure MFA service, users need to be licensed for Azure AD Premium or Azure AD Office 365 Apps – see here for more details
Getting Started
I ordered 2 tokens from Token 2 and received them a few days later, once I had them I had to request the the secret keys for the tokens by providing some verification information as well as the serial number of my new tokens. Token 2 provide the option to receive this information in a variety of formats and will also encrypt it with your own PGP key if you supply the public key. To make things super simple for Azure MFA they’ll send you the information in a csv format that you can import directly in the Azure portal.
Enabling the Tokens
As I said, importing the tokens is super simple, once Token 2 had supplied me with the csv, I simply had to edit the file, adding the upn of the user the token was to be assigned to, saved the csv and then imported it in the portal.

Importing in the Portal is easy, within the Azure Active Directory blade, scroll to MFA and then OATH tokens.
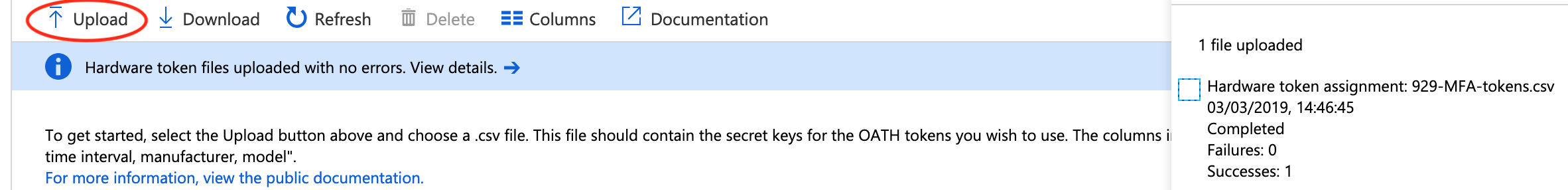
Click Upload and then select the csv, then wait a few seconds and click Refresh, you should see a message stating the file has uploaded successfully and the token should now be listed.
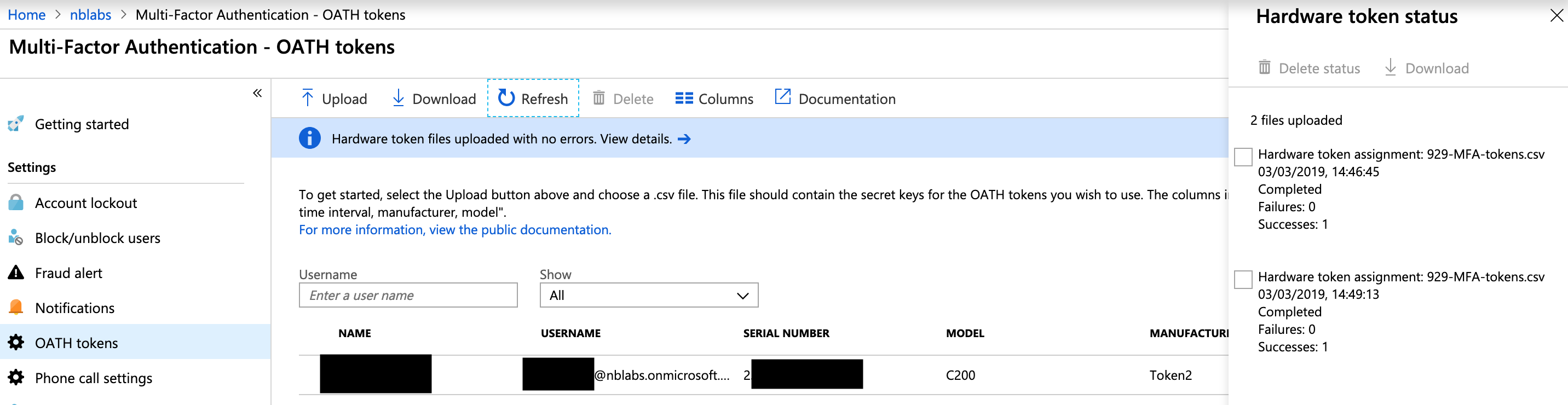
You’ll now need to activate the token, click the activate link and supply the current 6 digit code when prompted in the portal. Repeat the process for each token you add. At the end of the process I had 2 tokens activated for the same user in my Azure AD.
Once activated you’re good to go assuming the user you’ve added the token for is enabled for MFA either through a Conditional Access policy or via the MFA management portal.
Testing
Testing was simple enough, I’ve a Conditional Access policy enabled for the user I added both tokens for, which mandates MFA is required when logging into Office 365.
Upon entering my password I was immediately prompted to enter the code on my token.
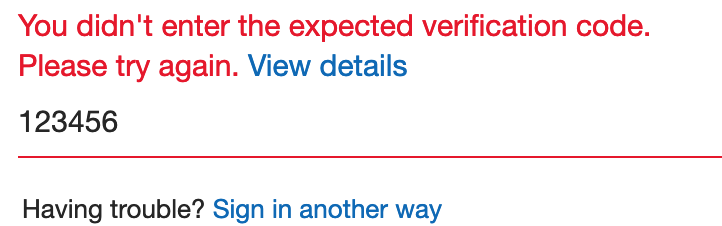
I selected one of the tokens at random, entered the 6 digit code and I signed in without issue. I then signed-out and repeated the process with the other token, again I signed in without any issue. Just to be thorough I signed-out again, signed in and this time entered 6 digits 1 through 6, I was informed by code wasn’t valid.
Summary
Hardware tokens and supporting multiple devices in Azure MFA is painless and simple to setup, it works really well and gives a great user experience. While I’ve talked here about using 2 hard tokens, you can mix and match, for the same user I could add the Microsoft Authenticator app as another option and if i had multiple smartphones I could add it multiple Authenticator apps. While not every user will need to make use of multiple devices I think adding the option is a great enhancement.
Hardware token registration in the Azure portal is super simple too and being able to import tokens in bulk makes it a really easy process.
